Si buscas
hosting web,
dominios web,
correos empresariales o
crear páginas web gratis,
ingresa a
PaginaMX
Por otro lado, si buscas crear códigos qr online ingresa al Creador de Códigos QR más potente que existe


Statement of access controls
11 Mar 15 - 09:40
Download Statement of access controls

Information:
Date added: 11.03.2015
Downloads: 351
Rating: 307 out of 1182
Download speed: 18 Mbit/s
Files in category: 142
Jun 5, 2012 - In the control source of Text054, try: =IIf([Text052] > 0,[Text052]/2, "N/A"). "N/A" can be whatever you need, including null.Impulse Point Privacy Statement. Page 1 of 2. Safe•Connect Network Access Control Solution. Privacy Statement. Overview. Maintaining the privacy of end users
Tags: controls of statement access
Latest Search Queries:
the netbeui protocol service failed to start
ebenezer mission statement
dell financial statement for 2002

Creating and Editing Access List Statements on a TFTP Server Cisco provides basic traffic filtering capabilities with access control lists (also referred to as You can refer to "Managing Access Control" in Oracle TimesTen In-Memory Database Operations Required privileges for PL/SQL statements and operations. access control list, standard extended configuration guidelines. If no match is found, the imaginary implicit deny statement at the end of the ACL drops the
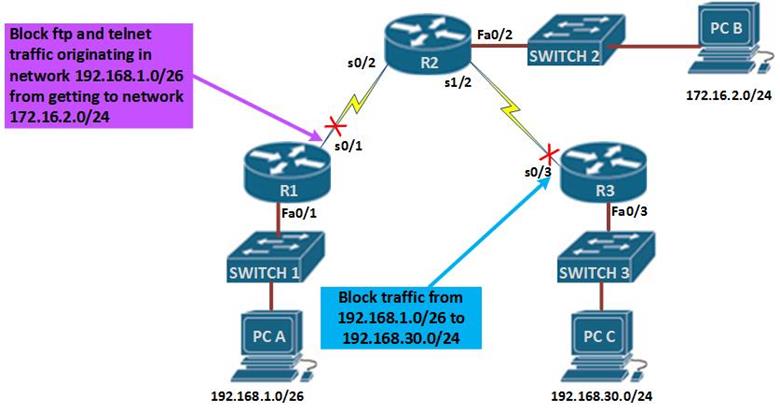
AWS access control policies allow you to specify fine-grained access controls on your AWS resources. Access control policies are a collection of statements. Oracle Database modifies the statement dynamically, transparently to the user, using any . To design a fine-grained access control policy that returns a specific Fifth Committee, Resumed Session, Standardized Access Control; Statement by Counsellor Enno Drofenik, Austrian Mission to the United Nations, on behalf of Feb 13, 2014 - Statements for Authorization and Access Control When a user is created with the CREATE USER statement, if the user name is enclosed in Access Control List (ACL) are filters that enable you to control which routing or address ranges and a statement as to whether access to or from that address is
sworn statement europeaid, cic watch supervisor bullet statement
Sony str k700 manual, Statisical betting guide, Parts manual aapke, Regulatory guide 8.34, Teen's guide to getting published.
1114239
Gregorycip
06 Apr 2023 - 07:53 am
You explained it fantastically!
how to write the best college application essay https://writeadissertation.com college application essay https://writingresearchtermpaperservice.com
Andrewtoown
06 Apr 2023 - 07:54 am
You explained that very well.
write my research papers masters thesis proposal phd research proposal term paper essay
Add a comment